Mishandling of Critical Evidence
As we progress through the digital age, courts are addressing questions of whether digital evidence is reliable. Many experts assert that it can be easily compromised, planted, or deleted without a trace.
Despite a previous precedent in the Second Circuit where a printed copy of a webpage was deemed “insufficient evidence,”[1] Ross’s judge allowed the case to rely almost exclusively on digital evidence, none of which was original.
Aside from Richard Bates’s testimony, the entire case against Ross relied on the digital evidence from his laptop. (In fact, Bates’s testimony contradicted the prosecution because he confirmed that Ross had passed Silk Road on to someone else in 2011[2]).
It was only after combing through thousand pages of trial transcripts and materials that the defense was able to start unveiling the questionable circumstances in which the evidence from the laptop was produced.
- At Ross’s arrest scene, FBI agent Thomas Kiernan was the first to take possession of the laptop and immediately started punching commands into the computer.[3] He plugged his USB drive in and began copying files without producing digital fingerprints to ensure the copies matched the originals.[4][5] By doing so, he overwrote some of the metadata for those files.[6][7]
- Kiernan “triaged” the laptop in the library for one or three hours (depending on when he was asked at trial)[8][9], he then “transported” it to Ross’s house about eight blocks away.[10] All that time, Kiernan was in sole possession of the laptop with nothing more than a few screenshots and photos to document what he did with it.
- Eventually, Kiernan “gave it over” to Christopher Beeson of RCFL, a private contractor in San Francisco.[11] Beeson also overwrote metadata by creating tar archives (like zip files) of commonly used directories on the laptop.[12]
- Beeson later admitted he was not familiar with the Guidelines for Evidence Collection and Archiving which clearly states not to run programs like tar that modify metadata.[13][14] During the tar process, Beeson was stopped by a failure[15] he was never able to determine the cause of, nor could he confirm he had properly copied the files.[16][17]
- Next, Beeson attempted to make a copy of the unencrypted partition of the laptop’s hard drive using “dd,” a “powerful tool” colloquially referred to as “disk destroyer” because if misused, it can cause irreparable harm to the data being manipulated.[18] While running “dd” several times, Beeson tried to generate a digital fingerprint but it kept failing each time.[19] Eventually, Beeson finished the copy of the hard drive without producing a digital fingerprint.[20]
- Two days after the laptop was initially seized, Beeson turned his attention to the data in the laptop’s RAM.[21] What happened to the computer over those two days remains unknown, but again there were problems. Kiernan and Beeson had overwritten or modified the data with all they had done up to that point.
- Beeson wasn’t “quite sure how to do [the] RAM capture” and had to ask for assistance and look up documentation.[22][23] He tried anyway and admittedly “crashed the computer,” losing unknown information and locking the laptop behind encryption.[24]
- Not one photo taken by Kiernan or Beeson to document their work showed the right time: they were all either three hours ahead, or 40 minutes behind.[25][26]
- Both agents ignored “order of volatility” guidelines,[27] and used obsolete, unreliable methods.[28]
Beeson eventually sent Kiernan the copy he had made of the laptop’s hard drive and the laptop itself,[29] which Kiernan called a useless “brick.”[30]
How true the “copy” Beeson extracted is to the original Kiernan seized from Ross is unknowable. Nor can it be known what exactly Kiernan did with the laptop before handing it over to Beeson, or what data was lost when Beeson crashed the computer. It is indisputable, however, that the laptop was not handled professionally, yet all evidence was admissible at trial.
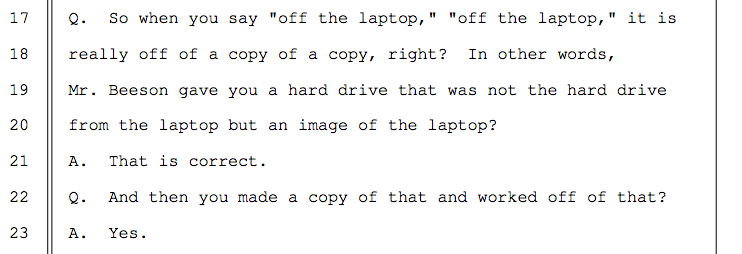
Kiernan also made another copy of Beeson’s copy[31] and the prosecution used this as the basis for their case against Ross. All evidence from the laptop used against Ross at trial was a screenshot of a copy of a copy.[32][33]
Read Also: Smeared with False Allegations
References
- ▲[1] – Social Media Law Bulletin article – November 17, 2014 (“Proving the Authenticity of a Digital Account at Trial: a Lesson from the Second Circuit”)
- ▲[2] – Trial transcript, day 6 (page 1139)
- ▲[3] – Trial transcript, day 5 (page 856)
- ▲[4] – Trial transcript, day 5 (page 857)
- ▲[5] – Trial transcript, day 6 (page 1077)
- ▲[6] – Trial transcript, day 5 (page 929)
- ▲[7] – Trial transcript, day 5 (page 947)
- ▲[8] – Trial transcript, day 5 (page 871)
- ▲[9] – Trial transcript, day 5 (page 916)
- ▲[10] – Trial transcript, day 5 (page 916)
- ▲[11] – Trial transcript, day 5 (page 871)
- ▲[12] – Trial transcript, day 6 (page 1210)
- ▲[13] – Trial transcript, day 6 (page 1211)
- ▲[14] – Guidelines for Evidence Collection and Archiving (page 4)
- ▲[15] – Trial transcript, day 6 (page 1212)
- ▲[16] –Trial transcript, day 6 (page 1212)
- ▲[17] – Trial transcript, day 6 (page 1213)
- ▲[18] – Trial transcript, day 6 (page 1214)
- ▲[19] – Trial transcript, day 6 (pages 1214-1215)
- ▲[20] –Trial transcript, day 6 (page 1215)
- ▲[21] – Trial transcript, day 6 (page 1216)
- ▲[22] – Trial transcript, day 7 (page 1244)
- ▲[23] – Trial transcript, day 7 (page 1247)
- ▲[24] – Trial transcript, day 7 (page 1248)
- ▲[25] – Trial transcript, day 5 (page 862)
- ▲[26] – Trial transcript, day 6 (page 1207)
- ▲[27] – Trial transcript, day 6 (page 1216)
- ▲[28] – Trial transcript, day 6 (page 1079)
- ▲[29] – Trial transcript, day 5 (page 872)
- ▲[30] – Trial transcript, day 6 (page 1078)
- ▲[31] – Trial transcript, day 6 (page 1044)
- ▲[32] – Trial transcript, day 6 (page 1044)
- ▲[33] – Trial transcript, day 6 (page 1009)
- ▲[34] – Ross’s appeal (page 6)
